(and you should too)
The Inti De Ceukelaire Interview
Learn why small businesses are protecting their systems by hiring good guy hackers.
By Patrick Clements, CEO SherpaDesk.com
Like many in the IT and Network Security business, you probably frequent sec-tech subreddits like /r/pwned, /r/netsec, and/or /r/whitehat.
I check out these forums regularly in order to stay on top of the latest news and developments around hacks and system vulnerabilities that could affect SherpaDesk (in order to nip them in the bud), so you'll probably understand my surprise and alarm when news of the so-called “Ticket Trick Hack" made it to the top of several tech subreddits.
The news of this hack was not only the buzz of Reddit, it was already starting to go viral with articles on well-known industry portals, its popularity fueled by the clever headline: “How I hacked hundreds of companies through their helpdesk”.
Inti De Ceukelaire
How I Hacked Hundreds of Companies
Through Their Helpdesk
Now, if this headline was being spewed out by a malicious hacker, it would have been every Network Administrator’s ultimate nightmare (and not just the ones managing cloud-based help desk ticketing systems).
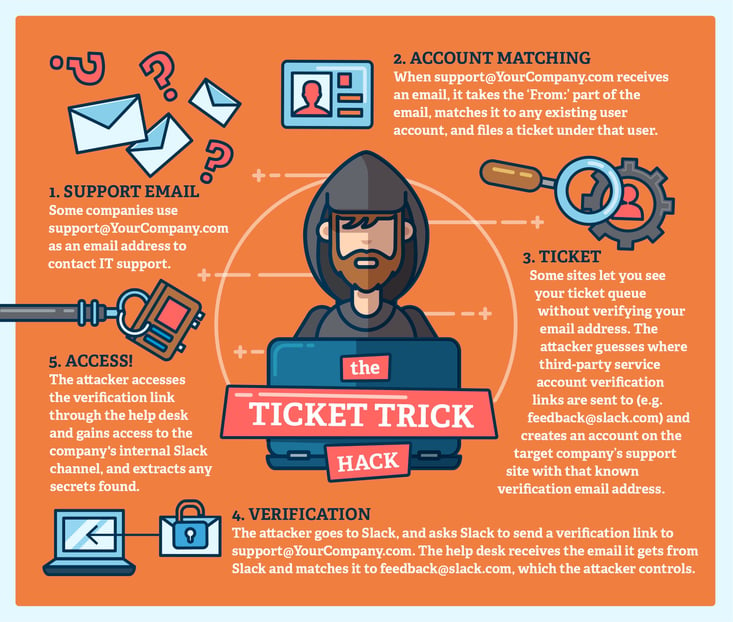
But this wasn’t the handiwork of some havoc-loving blackhat, this headline (as alarming as it may have sounded to me at the time) was the best way that self-proclaimed “Ethical Hacker” Inti De Ceukelaire figured he could get the word out of a serious vulnerability that could affect online help desks the world over. Since the hack focused on online ticketing systems in particular, he promptly named it “The Ticket Trick Hack” and even made a logo for it.
But How Does the Hack Actually Work?

The Help Desk Ticket Trick Hack
This vulnerability exploits the way that a lot of online help desk software interacts with popular third-party apps (for more details about what we at SherpaDesk are doing to protect our users from the Ticket Trick Hack, please check out our blog).
This and other exploits, like buying up expired domains from a well-known US presidential candidate's Tweets in order to switch where these expired URLs pointed to, have turned Inti De Ceukelaire into a bit of a celebrity and certainly a household name in network security circles. His instant celebrity has also helped shed light on the often-misunderstood world of the “Ethical Hacker".
What is an Ethical Hacker?
What exactly is an Ethical Hacker, and more importantly, why do we need them?We contacted Inti De Ceukelaire in his hometown of Oilsjt, Belgium to ask him precisely that.
1 - Hi Inti. What’s an ethical hacker? And, do you consider yourself to be one?
Hackers are people that come up with creative and unintended ways to compromise a system’s security. So-called “Ethical Hackers”, like me, do exactly the same. The main difference is that we try to help affected companies instead of hurting them. Quite simply, we let the affected companies know about their particular vulnerability so they can fix it.
2 - What’s the #1 tool or solution that a Network Administrator should be using today to reduce hacking?
A responsible disclosure program or a bug bounty program. Ironically, this will actually increase hacking (but luckily only the good parts of it). The idea is that Ethical Hackers will then be encouraged to test your security features and notify you of any issues they encounter.
3 - What are the 3 things Network Admins should be doing today to mitigate against a hack?
If there was a three-step method to mitigate against any hack, my profession would probably not exist. But if I would have to give my top 3 tips to prevent Network Admins from being hacked, they would be:
A-Patch your systems. Most attacks are caused by publicly known vulnerabilities that have existed for months or even years. Make sure to update all systems on the network at least once a week.
B-Increase security awareness within the company you work for. Even if your system security is foolproof, your co-workers are not. In most cases, companies get hacked because of human mistakes.
C-Assume the hacker is already inside. The insider threat is often overlooked: try to maintain strict security practices within the company. Employees should only have access to tools and resources they need.
4 - How vulnerable are most individuals, companies or national networks against cyber-attacks?
Everyone is vulnerable to cyber-attacks. When measuring the level of security, the question that should be asked is not whether hackers would ever be able to get in, the real question is how easy it is to get in and how long it would take them.
Any company can be vulnerable to a data breach. In my opinion, we should only blame companies that haven’t taken sufficient responsibility and measures to prevent it from happening in the first place.
Inti De Ceukelaire: Staring down bugs.
5 - What keeps you up at night?
Excitement. Whenever I’m working on a "target" I tend to forget about the time and just keep going all night. The adrenaline rush that comes with it doesn’t make falling asleep easy!
But generally speaking, I try not to worry too much about things that are out of my control, especially when it comes to cybersecurity. I try to do my part by making the internet a safer place, one bug at a time, which is very satisfying.
6 - Are you ever tempted by the dark side?
I started hacking when I was a teenager and a lot has changed since then. Back in those days, security wasn’t that big of a deal and it was fairly easy to compromise a website and mess around once inside. I never actually caused any damage or committed any harmful actions, but given the fact that ethical hacking was mostly unheard of back then, what I was doing was considered as illegal as any other type of hacking.
Fortunately, things have changed. I was lucky enough to learn about the ethical hacking community at a very young age and haven’t considered doing anything not 100% white hat ever since. As you can guess from the term, ethics are very important in our community. We encourage all sorts of hackers to join our team- but once they’ve joined, there’s no way back.
Even though I have never considered engaging in any criminal activities, it does not mean that it’s always easy being an ethical hacker. As a hacker, you sometimes possess an incredible amount of power. There are also malicious actors out there that offer thousands of dollars for finding vulnerabilities in popular software. Given the fact that most ethical hackers start from a very young age, they aren’t always able to deal with the power that comes with it.
7 - Thoughts on the future and whether AI, biometrics, and decentralized data will help reduce hacking efforts? Or will it make it worse?
Everything that is connected to an external network could be prone to hacking. The internet of things, self-driving cars and biometrics provide a far wider surface for hackers to attack. At the same time, the security industry has made quite a lot of progress over the past few years. Web applications are generally a lot safer than they were ten years ago. While things evolve, the battle between good and evil will go on forever.
8 - What's your top advice for small businesses as an ethical hacker?
Hire me. No, seriously: get your assets tested by ethical hackers. External security researchers can offer fresh insights on your company’s state of security. Bug bounty platforms like Intigriti (intigriti.be) and HackerOne (hackerone.com) are very accessible for small businesses and start-ups and will increase your security by a fair amount.
9 - What is the most common mistake or flaw in systems you discover as an ethical hacker?
Most of the times it comes down to input validation. Programmers that create systems expect a user to behave in a certain way. Hackers can abuse this form of trust to enter malicious code instead of one of the expected values.
10 - Social engineering vs technical hacks, what's more
prevalent nowadays?
Both happen all the time. Social engineering probably happens more because it’s often the easiest way to get into a company and requires no technical knowledge. That does not mean technical hacks are way less prevalent: they’re just more subtle and go unnoticed most of the time.
Thanks, Inti.





%201.png?width=559&height=559&name=close-up-women-working-with-devices%20(1)%201.png)