Data is the new gold and no other technology in existence strikes it as rich as the Internet of Things. By 2020, Gartner predicts that we will have 31 billion connected IoT devices (nearly 4x the number of people on the planet), all communicating an infinite amount of information back and forth at the speed of light.
Already, we need Artificial Intelligence (AI) to make sense of all this data; the human brain simply does not have the processing power. As the IoT and AI grow more sophisticated, the time will come when machines will tell us what to do instead of waiting to be told what to do. It’s a chapter straight out of a Sci-Fi book and this chapter will change the way we live and work.
One such change is our approach to strategic planning. It no longer suffices to roll out a three-year plan and measure progress as time passes. Technology revolutions like the IoT are too new and volatile for planning that far ahead. Instead, strategic planning must synchronize with the rate of change, which is constant.
Top IoT Challenges Driving Strategy
Scalability
One of the greatest challenges facing the IoT is scalability. As demand for IoT technology continues to rise, manufacturers are rushing the development process to meet demand. Decade-old code, that is laden with vulnerabilities is ending up in final designs and products that are released to market (already anticipating a barrage of patches). As opportunistic as the IoT is, the proliferation of data-sharing devices raises a question that does not yet have an answer.
How will we leverage and manage this vast (and growing) population of systems and devices while maintaining data security and privacy?
Security
Cyber attacks are only going to get worse in the years to come. The IoT is going to perpetuate this problem. According to Cisco’s 2018 Annual Cybersecurity Report, 31% of security professionals said their organizations have already experienced cyber attacks on their OT and IoT infrastructure. Why? Because IoT systems currently hinge on centralized back-end networks that control all devices. They’re easy targets, which should concern you. A single successful attack could mean failure on a massive scale. It is not enough to protect IoT devices. Security must be built into the software applications and network connections that link these devices.
Unfortunately, aside from the General Data Protection Regulation (GDPR), which went into effect in May of 2018, there is little regulation surrounding the IoT and practically no incentive for IoT device manufacturers to implement security measures.
Privacy & Data Ownership
Privacy and data ownership is also a chief concern for businesses planning to implement the IoT. For example, a company might not know if the data generated by their devices is technically owned or used by the device manufacturer. In other cases, a company may be unknowingly utilizing a sensor that is inadvertently collecting data “off the radar”. Poor planning and organization are to blame for these privacy and data ownership concerns.
Points of Change for IoT Strategy
Your IoT strategy serves as a plan for collecting, storing, protecting, analyzing, and utilizing data generated from your IoT devices. Moving forward, this strategy must also balance two critical objectives: Managing emerging risks and monetizing data.
As you routinely re-assess your IoT strategy, consider the following:
Broaden Your Perspective of How to Monetize IoT Data
Data doesn’t arrive in intelligent form; it must be made intelligent. One of the greatest mistakes companies make is failing to realize the vast opportunities made possible by the IoT and thus, failing to see ROI on IoT investments. They see data and business intelligence as a tool for getting more out of their reports instead of a crystal ball capable of predicting the future with incredible accuracy. Tools that utilize artificial intelligence will help you maximize the value of your data but, ultimately, success will depend on your strategy for collecting, organizing, and analyzing this information.
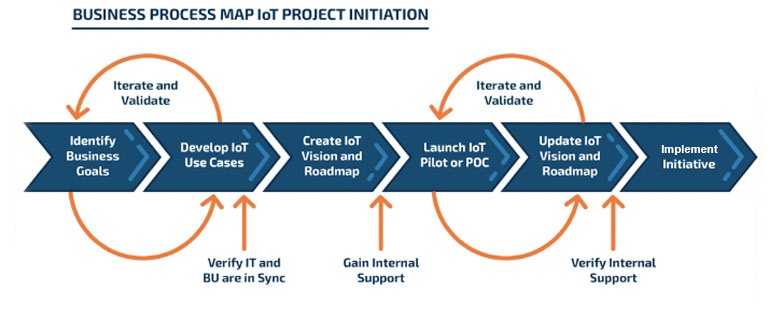
Adopt the Practice of IoT Mapping
The IoT is a digital jungle. You wouldn’t wander into the wilderness without trail blazes or a map to follow, would you? To truly monetize data, you must develop a process that clearly illustrates how each IoT solution will be utilized. Project mapping will help ensure that the technology you put into place aligns with the business objectives and use cases in which it is intended. Below is an example of what your process might look like. As you develop your own process, make it iterative and meticulously detail the following:
● Exactly what data is collected
● Where data is stored
● How data gets from device to storage
● Who can access data
● Who owns the data
● How data will be used
Implement Security Policies and Procedures
Only 49% of organizations surveyed have a formal policy in place and only about 1/3 patch their IoT devices within 24 hours of a fix release. In other words, these organizations are leaving the door wide open for cybercriminals. Until patches and security updates are considered at the manufacturing level, it is your sole responsibility to monitor these updates, apply patches, and police your own security. As you develop this policy, keep compliance with up-and-coming data, privacy, and security policies top of mind and consider incorporating the following.
Best practices:
● Make hardware tamper resistant. This includes restricting physical access, passwords, etc.
● Make timely firmware updates and patches: Develop a policy for immediately applying patches and upgrades to IoT devices.
● Secure the network: Protecting devices isn’t enough. You must safeguard the software and network connections that link these devices with two-factor authentication or context-aware authentication (CAA), and strong encryption and security protocols.
● Perform dynamic testing: Static testing doesn’t detect vulnerabilities that exist in off-the-shelf components like processors and memory. Dynamic testing will expose code weaknesses and underlying hardware defects.
● Secure the overall IoT network. When data assets are combined, personally identifiable information (PII) can emerge unexpectedly. Service mechanisms and authentication protocols will ensure that only authorized clients can discover IoT devices.
The IoT will transform our economy, give rise to new business models, and completely alter the way businesses operate. Organizations who successfully harness the power of data will optimize assets, conserve resources, reduce expenses, enhance services, generate revenue, increase engagement, and rise to the top. Will your organization strike it data rich or suffer a dry run? The desired outcome will depend on the agility of your IoT strategy.








comments